The Rise of Tech Scams In Australia
We all know that in Australia where technology is an integral part of daily life, the risk of falling prey to tech scams is ever-present. The convenience of our interconnected world comes with a dark side, and cybercriminals are becoming more sophisticated and aggressive in their tactics. Mr IT, a renowned name in “Mobile Computer Repairs Melbourne”, shares insights on how to recognise and protect yourself from these digital predators.
The statistics are staggering. According to the ACCC’s latest reports, Australians lose billions of dollars to scams annually, with tech support and remote access scams consistently ranking among the most financially damaging. These are not minor inconveniences; they are calculated attacks designed to exploit trust, induce panic, and cause significant financial and emotional distress. This guide will provide a comprehensive overview of these threats and empower you with the knowledge to defend your digital life.
Understanding Tech Scams
To effectively combat a threat, you must first understand it. Tech scams are a form of confidence trickery, updated for the digital age. Scammers prey on a common fear: the sudden failure of our essential technology and the loss of our precious data.
The Common Scamming Techniques
Tech scammers often initiate contact through a phone call or a computer pop-up, falsely claiming to represent reputable companies like Microsoft, Apple, Telstra, or even the NBN. These scammers, typically using heavy accents and high-pressure tactics, assert that your computer has been infected with a virus or that your internet connection has been compromised. They exploit the fear of losing digital data and manipulate users into believing their computer is at risk.
Beyond these classic methods, their arsenal has expanded to include:
- Phishing and Spear Phishing Emails: Deceptively legitimate-looking emails that prompt you to click malicious links or download infected attachments.
- Smishing (SMS Phishing): Urgent text messages about account security, package deliveries, or bank alerts that link to fake websites designed to steal your credentials.
- Malvertising: Malicious ads on legitimate websites that, when clicked, can install malware or redirect you to a scam page.
- Social Media Scams: Fake profiles or direct messages on platforms like Facebook and Instagram, often impersonating friends or official support channels.
Why These Scams Work
Scammers are masters of psychological manipulation. They rely on several key tactics:
- Creating Urgency and Fear: They tell you that your data is being stolen right now or that your bank account is being drained. This panic short-circuits rational thinking.
- Appealing to Authority: By claiming to be from Microsoft or another trusted entity, they create a false sense of security and legitimacy.
- Using Technobabble: They overwhelm you with technical jargon and fake error codes to make you feel ignorant and helpless, positioning themselves as the only solution.
The Scammer’s Playbook in Australia
The scammer’s goal is to make you download a “support software” that allows them access to your computer. Once inside, they create an illusion of a virus-infested system using fabricated errors and false diagnostics, creating panic. This fear-mongering is a tactic to extort money by demanding your credit card information under the guise of resolving these fictitious problems.
Here’s how they build the illusion:
- The “Proof”: They may ask you to open Windows Event Viewer or the Command Prompt. These tools often show normal system notifications and files, which the scammer will falsely label as “critical errors,” “foreign connections,” or “virus traces.”
- The Fake Scan: They will run a mock scan that inevitably finds hundreds or thousands of “infections.”
- The Hard Sell: With the “evidence” presented, they escalate the pressure. This fear-mongering is a tactic to extort money by demanding your credit card information under the guise of resolving these fictitious problems. They may ask for a one-time fee for a “fix” or, more dangerously, try to sell you a multi-year “security subscription” costing thousands of dollars.
Safeguarding Your Computer From Tech Scams In Australia
Prevention is always the best strategy. Building a robust digital defence involves a combination of the right tools and, more importantly, the right mindset.
Immediate Steps for Protection
- Disconnecting from the Scam: If you receive a suspicious call, the safest course of action is to hang up immediately. Engaging with the scammer can lead to further risks.
- Managing pop-Ups: In the event of a virus alert pop-up, don’t click or call any provided number. Instead, perform an anti-virus scan to check for real threats.
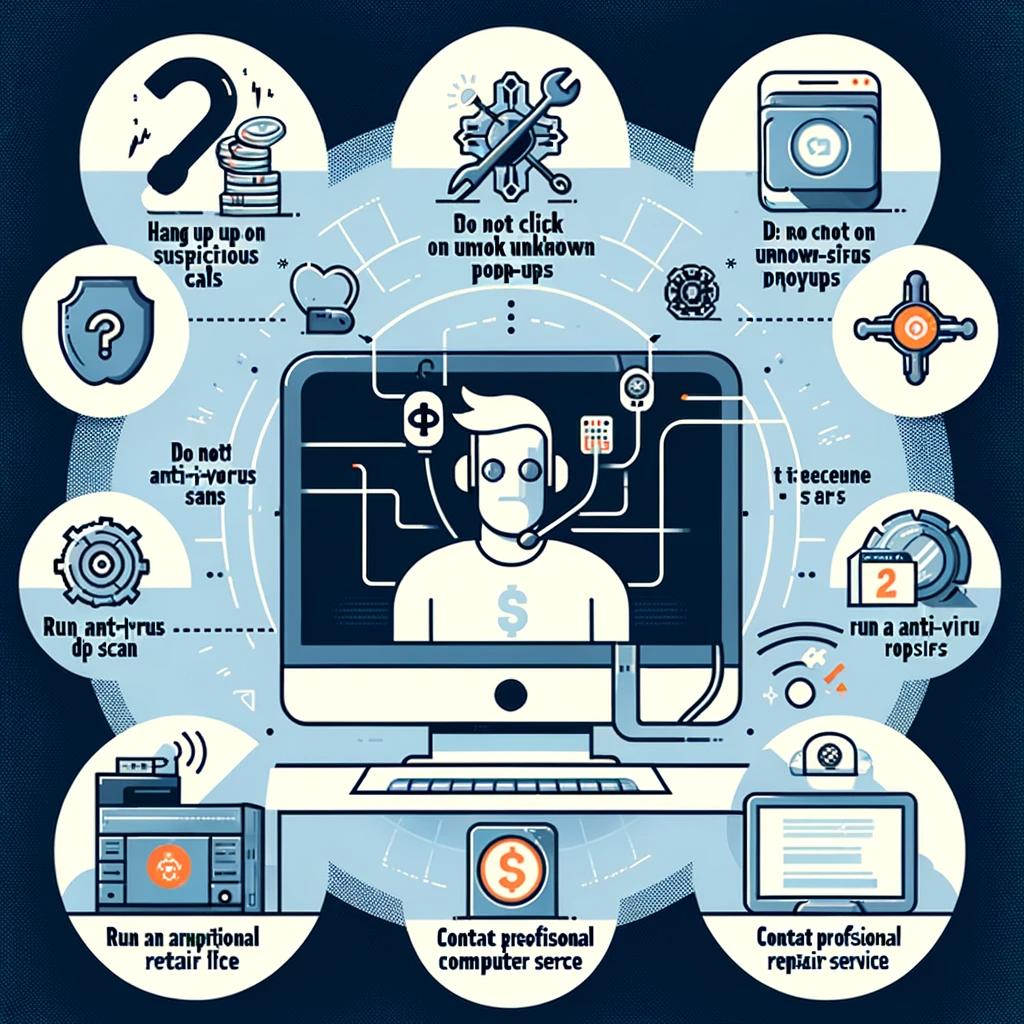
Recognising Legitimate Tech Support
Remember, legitimate companies, especially those as prominent as Microsoft, will never make unsolicited calls for tech support. This knowledge is key in differentiating between genuine assistance and a scam.
Post-Scam Recovery
If the worst happens and you fall victim, acting quickly can significantly limit the damage.
Handling Financial Security
If you’ve been scammed, the first priority is your money. Contact your bank or financial institution immediately to report the fraudulent transaction. They can often reverse any unauthorised charges and will take steps to secure your financial accounts, such as cancelling your cards. This step is crucial in mitigating the damage and aiding in the scammer’s apprehension.
Securing Your Digital Identity and Devices
- Disconnect: Immediately disconnect the compromised computer from the internet to prevent the scammer from having further access.
- Change Passwords: Change the passwords for all your critical accounts, especially email, banking, and social media. Do this from a separate, trusted device.
- Report the Crime: Report the incident to Scamwatch and the Australian Cyber Security Centre (ACSC). This helps authorities track scam operations and warn others.
- Run a Full Security Scan: Use a reputable antivirus program to perform a deep, full-system scan to find and remove any malicious software the scammer may have installed.
Securing Your Computer with Mr IT
Following a scam, it’s imperative to ensure your computer is clean and secure. Seeking assistance from trusted computer repair services like Mr IT, known for competitive “Computer Repairs Melbourne Prices”, is advisable. They can thoroughly check your system and remove any malicious software or backdoors left by the scammer.

Staying Safe in this Digital Age For Melbournians
For residents of Melbourne, being aware of tech scams is critical. Companies like Mr IT, a leader in “Mobile Computer Repairs Melbourne”, emphasize the importance of education and vigilance in the fight against these digital threats. By staying informed and cautious, you can safeguard not only your computer but your overall digital well-being.
To Find Out more about our services and how we can help you contact us here
